This pandemic has brought major disruption to the world, forcing millions to work from home. With remote working as the new “business as usual”, it is only natural that video conferencing services, like Zoom, are on the rise. However, this disruption has also brought out a slew of hackers. From built-in attention-tracking features to “Zoombombings”, Zoom has fallen victim to these types of attacks and has taken a lot of heat over the past month for its security practices.
In Zoom’s defense, Zoom increased from 10 Million users to 200 million users overnight. They probably weren’t expecting a surge like that and weren’t ready to scale their security protocols at that level and that quickly. Also, any other video conferencing service experiencing this much growth would be having the same scrutiny right now. Zoom is actively fixing bugs and releasing updates to correct some of these issues. There are also precautions the user can take to minimize security threats as well.
In this blog, we will walk you through some of the recommended settings we have been advising our internal teams to take. There are a lot of setting features available, so let us give you suggested actions you can take to minimize security threats and then we will breakdown which setting options are must-haves vs. ones that are not needed.
6 actions that YOU can take to minimize security threats
1. Understand the different type of meetings
It is good to understand the different types of meeting options available so that you can use the most secure options based on your needs.
-
- Personal Meeting IDs (PMI) is a number you define. Generally, it is better practice to not use these since hackers are guessing the Meeting IDs. However, people like to use these since it is easy to remember so if you choose to use it, then you should at least have the PMI password enabled.
- Scheduled meeting is one you set ahead of time through the Zoom schedule tool or through the add-in in Outlook. You can use PMI for this type of meeting or not.
- Instant meeting is one where you can send a direct email or other means, non-scheduled, to have a meeting. You can use PMI for this type of meeting or not.
2. Minimize use of Personal Meeting ID (PMI)
As we mentioned above, Personal Meeting ID makes it easier for hackers to guess. We recommend using a per-meeting ID, exclusive to a single meeting when you can. Zoom's support page offers a video walk-through on how to generate a random meeting ID for extra security. If you need to use PMI for scheduled or instant meetings, at a minimum, make sure you add a password (see #4).
3. Always install the updates
Zoom is actively working to enhance their security. Install patches when prompted by the Zoom tools to do so. It only takes 5 min and could keep a hacker out!
4. Require passwords
At a minimum, add a password to your meetings. The specific settings are outlined in detail under #6.
5. Leverage waiting rooms
For one more layer, have the attendees go to the “Waiting Room” and admit them when recognized. This is included in the list below. A lot of schools have started implementing this for the safety of the children. Professional services should consider doing this too.
6. Check your settings
To get to settings, go to settings in the left-hand column. You have three tabs, Meeting, Recording, and Telephone, at the top. Below is a screenshot of how to get to your settings.
Now for the list of security options in your "Settings". This list can be overwhelming, so let us break it down for you. We have a numbered list with a visual indicating if you should enable or disable certain settings. A more detailed description is provided below.
Note: These are not ALL the settings available, just the security-related ones. Most of the settings listed below are listed under “schedule meeting” but #11 and #12 are under “In Meeting (Basic)” and “In Meeting (Advanced)”, respectively.
Settings Options
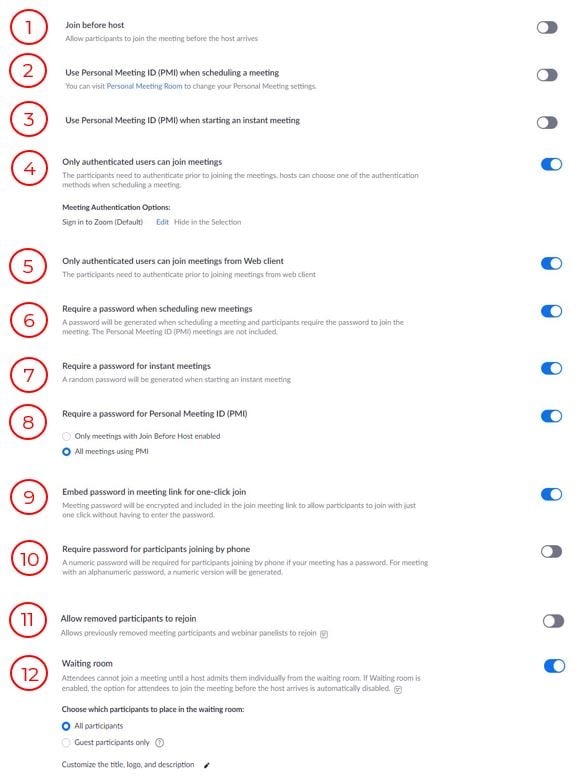
- Join before host
NO, NOT NECESSARY – This setting does not allow anyone in the meeting till you join. This is not very helpful from a security standpoint since hackers can still join once the meeting has started. It would be better to use the “Waiting Room” below (see #12).
. - Use Personal Meeting ID (PMI) when scheduling a meeting
NO, NOT RECOMMENDED – This setting allows you to define the meeting number. You can use this to make your recurring meetings easier to remember. This won’t be very helpful for adding security as it uses the same meeting number every time. If you use these, please enable a password (see #8).
. - Use Personal Meeting ID (PMI) when starting an instant meeting
NO, NOT NECESSARY –This is like PMI for a scheduled meeting. However, this setting is dependent on #7. It #7 is on, #3 has to be off. It’s more important that #7 is enabled, so this should be disabled.
. - Only authenticated users can join meetings
YES, WHY NOT – This is a good setting. It is supposed to prompt attendees for the authentication prior to joining. If you have this set, you won’t even notice its function, so it doesn’t cause any inconveniences to take extra precaution. You can change the ‘option’ by hitting edit and enter a new string where it says Sign into Zoom.
. - Only authenticated users can join meetings from Web client
YES, WHY NOT – Like the above but for Web joiners. Again, a good idea to set it.
. - Require a password when scheduling new meetings
YES, IT’S A MUST – Enable this. This is the best way to secure the meeting and its content.
. - Require a password for instant meetings
YES, IT’S A MUST – Enable this. This is the best way to secure the meeting and its content.
. - Require a password for Personal Meeting ID (PMI)
YES, IT’S A MUST – Enable this. This is the best way to secure the meeting and its content. It will give you two options when you turn this option on; click “All meetings using PMI”.
. - Embed password in meeting link for one-click join
YES, IT’S A MUST – It makes joining your meeting for folks with an invite easy but make it harder to hack.
. - Require password for participants joining by phone
NO, IT DEPENDS – This is a personal preference. If you are concerned about information security in the meeting this is a must-have setting.
. - Allow removed participants to rejoin – In Meeting (Basic) settings:
NO, DEFINITELY NOT – If you had to remove someone then why on earth would you want them back in your meeting.
. - Waiting room - In Meeting (Advanced) Settings:
YES, IT’S A MUST – This is one of the best ways to keep unwanted attendees out of the meeting. Don’t let them in! That said this can be tricky with folks dialing in from phones so use with some caution it may take some getting used to.
.
In Conclusion
Zoom is our preferred video conferencing service and we believe Zoom is as “safe” as any of the conferencing options out there. If the tool of choice was Go To Meeting or Skype, they would be dealing with the same security issues. While there are security protocols outside of the user’s control, there are several things you can do as a user to help minimize hacker attacks.
At Veritas, we understand the office dynamic has changed. As we transition into this new reality, we want to share what we are learning to help others. Taking clients through transformational change is not new to us. All of our services, including Technology Solutions, are grounded in transformation. For more information on how we can help you through this difficult time, please connect with us or subscribe to our blog to stay connected.

